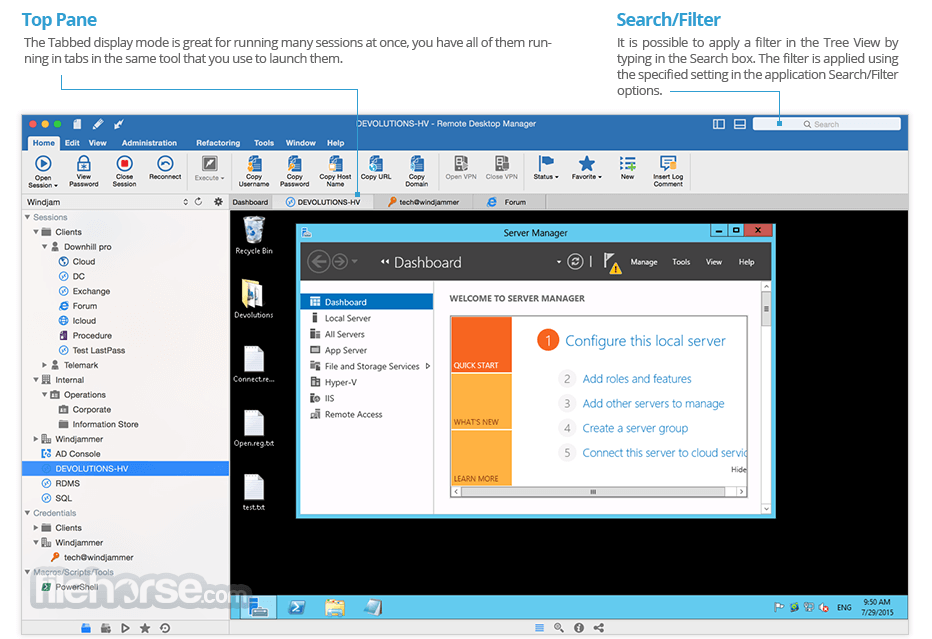
-->
Version 1.3.3.0 5.4 MB Release Notes The Remote Desktop Manager Agent can run commands on remote hosts, but what is really useful is that it can send commands to multiple hosts at the same time. Microsoft Remote Desktop Connection Manager Microsoft has retired MRDCM software and following link is not having download anymore. There is some serious vulnerabilities found in this software, although it is still very popular Remote Desktop Connection Manager tool. Remote Desktop Manager Enterprise 2019.1 features some exciting new additions and improvements — many of which were recommended by our community. Here is what you can look forward to: Complete UI relooking (SVG). We don't have any change log information yet for version 2.7.1406.0 of Remote Desktop Connection Manager. Sometimes publishers take a little while to make this information available, so please check back in a few days to see if it has been updated. Patch Name: Setup.RemoteDesktopManagerFree.2019.1.6.0.msi: Patch Description: Remote Desktop Manager (2019.1.6.0) Bulletin Id: TU-774: Bulletin Title: Updates for.
Applies To: Windows Server 2016, Windows Server 2019
When it comes to supported configurations for Remote Desktop Services environments, the largest concern tends to be version interoperability. Most environments include multiple versions of Windows Server - for example, you may have an existing Windows Server 2012 R2 RDS deployment but want to upgrade to Windows Server 2016 to take advantage of the new features (like support for OpenGLOpenCL, Discrete Device Assignment, or Storage Spaces Direct). The question then becomes, which RDS components can work with different versions and which need to be the same?
So with that in mind, here are basic guidelines for supported configurations of Remote Desktop Services in Windows Server.
Note
Make sure to review the system requirements for Windows Server 2016 and system requirements for Windows Server 2019.
Best practices
Remote Desktop Manager 2019 1 4 0 6 Months
Use Windows Server 2019 for your Remote Desktop infrastructure (the Web Access, Gateway, Connection Broker, and license server). Windows Server 2019 is backward-compatible with these components, which means a Windows Server 2016 or Windows Server 2012 R2 RD Session Host can connect to a 2019 RD Connection Broker, but not the other way around.
For RD Session Hosts - all Session Hosts in a collection need to be at the same level, but you can have multiple collections. You can have a collection with Windows Server 2016 Session Hosts and one with Windows Server 2019 Session Hosts.
If you upgrade your RD Session Host to Windows Server 2019, also upgrade the license server. Remember that a 2019 license server can process CALs from all previous versions of Windows Server, down to Windows Server 2003.
Follow the upgrade order recommended in Upgrading your Remote Desktop Services environment.
If you are creating a highly available environment, all of your Connection Brokers need to be at the same OS level.
RD Connection Brokers
Windows Server 2016 removes the restriction for the number of Connection Brokers you can have in a deployment when using Remote Desktop Session Hosts (RDSH) and Remote Desktop Virtualization Hosts (RDVH) that also run Windows Server 2016. The following table shows which versions of RDS components work with the 2016 and 2012 R2 versions of the Connection Broker in a highly available deployment with three or more Connection Brokers.
| 3+ Connection Brokers in HA | RDSH or RDVH 2019 | RDSH or RDVH 2016 | RDSH or RDVH 2012 R2 |
|---|---|---|---|
| Windows Server 2019 Connection Broker | Supported | Supported | Supported |
| Windows Server 2016 Connection Broker | N/A | Supported | Supported |
| Windows Server 2012 R2 Connection Broker | N/A | N/A | Not Supported |
Support for graphics processing unit (GPU) acceleration
Remote Desktop Services support systems equipped with GPUs. Applications that require a GPU can be used over the remote connection. Additionally, GPU-accelerated rendering and encoding can be enabled for improved app performance and scalability.
Remote Desktop Services Session Hosts and single-session client operating systems can take advantage of the physical or virtual GPUs presented to the operating system in many ways, including the Azure GPU optimized virtual machine sizes, GPUs available to the physical RDSH server, and GPUs presented to the VMs by supported hypervisors.

See Which graphics virtualization technology is right for you? for help figuring out what you need. For specific information about DDA, check out Plan for deploying Discrete Device Assignment.
GPU vendors may have a separate licensing scheme for RDSH scenarios or restrict GPU use on the server OS, verify the requirements with your favorite vendor.
GPUs presented by a non-Microsoft hypervisor or Cloud Platform must have drivers digitally-signed by WHQL and supplied by the GPU vendor.
Remote Desktop Session Host support for GPUs
The following table shows the scenarios supported by different versions of RDSH hosts.
| Feature | Windows Server 2008 R2 | Windows Server 2012 R2 | Windows Server 2016 | Windows Server 2019 |
|---|---|---|---|---|
| Use of hardware GPU for all RDP sessions | No | Yes | Yes | Yes |
| H.264/AVC hardware encoding (if suppported by the GPU) | No | No | Yes | Yes |
| Load balancing between multiple GPUs presented to the OS | No | No | No | Yes |
| H.264/AVC encoding optimizations for minimizing bandwidth usage | No | No | No | Yes |
| H.264/AVC support for 4K resolution | No | No | No | Yes |
VDI support for GPUs
The following table shows support for GPU scenarios in the client OS.
| Feature | Windows 7 SP1 | Windows 8.1 | Windows 10 |
|---|---|---|---|
| Use of hardware GPU for all RDP sessions | No | Yes | Yes |
| H.264/AVC hardware encoding (if suppported by the GPU) | No | No | Windows 10 1703 and later |
| Load balancing between multiple GPUs presented to the OS | No | No | Windows 10 1803 and later |
| H.264/AVC encoding optimizations for minimizing bandwidth usage | No | No | Windows 10 1803 and later |
| H.264/AVC support for 4K resolution | No | No | Windows 10 1803 and later |
RemoteFX 3D Video Adapter (vGPU) support
Note
Because of security concerns, RemoteFX vGPU is disabled by default on all versions of Windows starting with the July 14, 2020 Security Update. To learn more, see KB 4570006.
Remote Desktop Services supports RemoteFX vGPUs when VM is running as a Hyper-V guest on Windows Server 2012 R2 or Windows Server 2016. The following guest operating systems have RemoteFX vGPU support:
- Windows 7 SP1
- Windows 8.1
- Windows 10 1703 or later
- Windows Server 2016 in a single-session deployment only
Discrete Device Assignment support
Remote Desktop Services supports Physical GPUs presented with Discrete Device Assignment from Windows Server 2016 or Windows Server 2019 Hyper-V hosts. See Plan for deploying Discrete Device Assignment for more details.
VDI deployment – supported guest OSes
Windows Server 2016 and Windows Server 2019 RD Virtualization Host servers support the following guest OSes:
- Windows 10 Enterprise
- Windows 8.1 Enterprise
- Windows 7 SP1 Enterprise
Note
- Remote Desktop Services doesn't support heterogeneous session collections. The OSes of all VMs in a collection must be the same version.
- You can have separate homogeneous collections with different guest OS versions on the same host.
- The Hyper-V host used to run VMs must be the same version as the Hyper-V host used to create the original VM templates.
Single sign-on
Windows Server 2016 and Windows Server 2019 RDS supports two main SSO experiences:
- In-app (Remote Desktop application on Windows, iOS, Android, and Mac)
- Web SSO
Using the Remote Desktop application, you can store credentials either as part of the connection info (Mac) or as part of managed accounts (iOS, Android, Windows) securely through the mechanisms unique to each OS.
To connect to desktops and RemoteApps with SSO through the inbox Remote Desktop Connection client on Windows, you must connect to the RD Web page through Internet Explorer. The following configuration options are required on the server side. No other configurations are supported for Web SSO:
- RD Web set to Forms-Based Authentication (Default)
- RD Gateway set to Password Authentication (Default)
- RDS Deployment set to 'Use RD Gateway credentials for remote computers' (Default) in the RD Gateway properties
Note
Due to the required configuration options, Web SSO is not supported with smartcards. Users who login via smartcards might face multiple prompts to login.
For more information about creating VDI deployment of Remote Desktop Services, check out Supported Windows 10 security configurations for Remote Desktop Services VDI.
Using Remote Desktop Services with application proxy services
You can use Remote Desktop Services with Azure AD Application Proxy. Remote Desktop Services does not support using Web Application Proxy, which is included in Windows Server 2016 and earlier versions.
-->Use these steps when a Remote Desktop client can't connect to a remote desktop but doesn't provide messages or other symptoms that would help identify the cause.
Check the status of the RDP protocol
Check the status of the RDP protocol on a local computer
See Which graphics virtualization technology is right for you? for help figuring out what you need. For specific information about DDA, check out Plan for deploying Discrete Device Assignment.
GPU vendors may have a separate licensing scheme for RDSH scenarios or restrict GPU use on the server OS, verify the requirements with your favorite vendor.
GPUs presented by a non-Microsoft hypervisor or Cloud Platform must have drivers digitally-signed by WHQL and supplied by the GPU vendor.
Remote Desktop Session Host support for GPUs
The following table shows the scenarios supported by different versions of RDSH hosts.
| Feature | Windows Server 2008 R2 | Windows Server 2012 R2 | Windows Server 2016 | Windows Server 2019 |
|---|---|---|---|---|
| Use of hardware GPU for all RDP sessions | No | Yes | Yes | Yes |
| H.264/AVC hardware encoding (if suppported by the GPU) | No | No | Yes | Yes |
| Load balancing between multiple GPUs presented to the OS | No | No | No | Yes |
| H.264/AVC encoding optimizations for minimizing bandwidth usage | No | No | No | Yes |
| H.264/AVC support for 4K resolution | No | No | No | Yes |
VDI support for GPUs
The following table shows support for GPU scenarios in the client OS.
| Feature | Windows 7 SP1 | Windows 8.1 | Windows 10 |
|---|---|---|---|
| Use of hardware GPU for all RDP sessions | No | Yes | Yes |
| H.264/AVC hardware encoding (if suppported by the GPU) | No | No | Windows 10 1703 and later |
| Load balancing between multiple GPUs presented to the OS | No | No | Windows 10 1803 and later |
| H.264/AVC encoding optimizations for minimizing bandwidth usage | No | No | Windows 10 1803 and later |
| H.264/AVC support for 4K resolution | No | No | Windows 10 1803 and later |
RemoteFX 3D Video Adapter (vGPU) support
Note
Because of security concerns, RemoteFX vGPU is disabled by default on all versions of Windows starting with the July 14, 2020 Security Update. To learn more, see KB 4570006.
Remote Desktop Services supports RemoteFX vGPUs when VM is running as a Hyper-V guest on Windows Server 2012 R2 or Windows Server 2016. The following guest operating systems have RemoteFX vGPU support:
- Windows 7 SP1
- Windows 8.1
- Windows 10 1703 or later
- Windows Server 2016 in a single-session deployment only
Discrete Device Assignment support
Remote Desktop Services supports Physical GPUs presented with Discrete Device Assignment from Windows Server 2016 or Windows Server 2019 Hyper-V hosts. See Plan for deploying Discrete Device Assignment for more details.
VDI deployment – supported guest OSes
Windows Server 2016 and Windows Server 2019 RD Virtualization Host servers support the following guest OSes:
- Windows 10 Enterprise
- Windows 8.1 Enterprise
- Windows 7 SP1 Enterprise
Note
- Remote Desktop Services doesn't support heterogeneous session collections. The OSes of all VMs in a collection must be the same version.
- You can have separate homogeneous collections with different guest OS versions on the same host.
- The Hyper-V host used to run VMs must be the same version as the Hyper-V host used to create the original VM templates.
Single sign-on
Windows Server 2016 and Windows Server 2019 RDS supports two main SSO experiences:
- In-app (Remote Desktop application on Windows, iOS, Android, and Mac)
- Web SSO
Using the Remote Desktop application, you can store credentials either as part of the connection info (Mac) or as part of managed accounts (iOS, Android, Windows) securely through the mechanisms unique to each OS.
To connect to desktops and RemoteApps with SSO through the inbox Remote Desktop Connection client on Windows, you must connect to the RD Web page through Internet Explorer. The following configuration options are required on the server side. No other configurations are supported for Web SSO:
- RD Web set to Forms-Based Authentication (Default)
- RD Gateway set to Password Authentication (Default)
- RDS Deployment set to 'Use RD Gateway credentials for remote computers' (Default) in the RD Gateway properties
Note
Due to the required configuration options, Web SSO is not supported with smartcards. Users who login via smartcards might face multiple prompts to login.
For more information about creating VDI deployment of Remote Desktop Services, check out Supported Windows 10 security configurations for Remote Desktop Services VDI.
Using Remote Desktop Services with application proxy services
You can use Remote Desktop Services with Azure AD Application Proxy. Remote Desktop Services does not support using Web Application Proxy, which is included in Windows Server 2016 and earlier versions.
-->Use these steps when a Remote Desktop client can't connect to a remote desktop but doesn't provide messages or other symptoms that would help identify the cause.
Check the status of the RDP protocol
Check the status of the RDP protocol on a local computer
To check and change the status of the RDP protocol on a local computer, see How to enable Remote Desktop.
Note
If the remote desktop options are not available, see Check whether a Group Policy Object is blocking RDP.
Check the status of the RDP protocol on a remote computer
Important
Follow this section's instructions carefully. Serious problems can occur if the registry is modified incorrectly. Before you start modifying the registry, back up the registry so you can restore it in case something goes wrong.
To check and change the status of the RDP protocol on a remote computer, use a network registry connection:
- First, go to the Start menu, then select Run. In the text box that appears, enter regedt32.
- In the Registry Editor, select File, then select Connect Network Registry.
- In the Select Computer dialog box, enter the name of the remote computer, select Check Names, and then select OK.
- Navigate to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server.
- If the value of the fDenyTSConnections key is 0, then RDP is enabled.
- If the value of the fDenyTSConnections key is 1, then RDP is disabled.
- To enable RDP, change the value of fDenyTSConnections from 1 to 0.
Check whether a Group Policy Object (GPO) is blocking RDP on a local computer
If you can't turn on RDP in the user interface or the value of fDenyTSConnections reverts to 1 after you've changed it, a GPO may be overriding the computer-level settings.
To check the group policy configuration on a local computer, open a Command Prompt window as an administrator, and enter the following command:
After this command finishes, open gpresult.html. In Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop ServicesRemote Desktop Session HostConnections, find the Allow users to connect remotely by using Remote Desktop Services policy.
Remote Desktop Manager 2019 1 4 0 6 177
If the setting for this policy is Enabled, Group Policy is not blocking RDP connections.
If the setting for this policy is Disabled, check Winning GPO. This is the GPO that is blocking RDP connections.
Check whether a GPO is blocking RDP on a remote computer
To check the Group Policy configuration on a remote computer, the command is almost the same as for a local computer:
The file that this command produces (gpresult-.html) uses the same information format as the local computer version (gpresult.html) uses.
Modifying a blocking GPO
You can modify these settings in the Group Policy Object Editor (GPE) and Group Policy Management Console (GPM). For more information about how to use Group Policy, see Advanced Group Policy Management.
To modify the blocking policy, use one of the following methods:
- In GPE, access the appropriate level of GPO (such as local or domain), and navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections > Allow users to connect remotely by using Remote Desktop Services.
- Set the policy to either Enabled or Not configured.
- On the affected computers, open a command prompt window as an administrator, and run the gpupdate /force command.
- In GPM, navigate to the organizational unit (OU) in which the blocking policy is applied to the affected computers and delete the policy from the OU.
Check the status of the RDP services
On both the local (client) computer and the remote (target) computer, the following services should be running:
- Remote Desktop Services (TermService)
- Remote Desktop Services UserMode Port Redirector (UmRdpService)
You can use the Services MMC snap-in to manage the services locally or remotely. You can also use PowerShell to manage the services locally or remotely (if the remote computer is configured to accept remote PowerShell cmdlets).
On either computer, if one or both services are not running, start them.
Note
If you start the Remote Desktop Services service, click Yes to automatically restart the Remote Desktop Services UserMode Port Redirector service.
Check that the RDP listener is functioning
Important
Lite 1.4
Follow this section's instructions carefully. Serious problems can occur if the registry is modified incorrectly. Before you starty modifying the registry, back up the registry so you can restore it in case something goes wrong.
Check the status of the RDP listener
For this procedure, use a PowerShell instance that has administrative permissions. For a local computer, you can also use a command prompt that has administrative permissions. However, this procedure uses PowerShell because the same cmdlets work both locally and remotely.
To connect to a remote computer, run the following cmdlet:
Enter qwinsta.
If the list includes rdp-tcp with a status of Listen, the RDP listener is working. Proceed to Check the RDP listener port. Otherwise, continue at step 4.
Export the RDP listener configuration from a working computer.
- Sign in to a computer that has the same operating system version as the affected computer has, and access that computer's registry (for example, by using Registry Editor).
- Navigate to the following registry entry:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp - Export the entry to a .reg file. For example, in Registry Editor, right-click the entry, select Export, and then enter a filename for the exported settings.
- Copy the exported .reg file to the affected computer.
To import the RDP listener configuration, open a PowerShell window that has administrative permissions on the affected computer (or open the PowerShell window and connect to the affected computer remotely).
To back up the existing registry entry, enter the following cmdlet:
To remove the existing registry entry, enter the following cmdlets:
To import the new registry entry and then restart the service, enter the following cmdlets:
Replace with the name of the exported .reg file.
Test the configuration by trying the remote desktop connection again. If you still can't connect, restart the affected computer.
If you still can't connect, check the status of the RDP self-signed certificate.
Check the status of the RDP self-signed certificate
- If you still can't connect, open the Certificates MMC snap-in. When you are prompted to select the certificate store to manage, select Computer account, and then select the affected computer.
- In the Certificates folder under Remote Desktop, delete the RDP self-signed certificate.
- On the affected computer, restart the Remote Desktop Services service.
- Refresh the Certificates snap-in.
- If the RDP self-signed certificate has not been recreated, check the permissions of the MachineKeys folder.
Check the permissions of the MachineKeys folder
- On the affected computer, open Explorer, and then navigate to C:ProgramDataMicrosoftCryptoRSA.
- Right-click MachineKeys, select Properties, select Security, and then select Advanced.
- Make sure that the following permissions are configured:
- BuiltinAdministrators: Full control
- Everyone: Read, Write
Check the RDP listener port
On both the local (client) computer and the remote (target) computer, the RDP listener should be listening on port 3389. No other applications should be using this port.
Important
Follow this section's instructions carefully. Serious problems can occur if the registry is modified incorrectly. Before you starty modifying the registry, back up the registry so you can restore it in case something goes wrong.
To check or change the RDP port, use the Registry Editor:
- Go to the Start menu, select Run, then enter regedt32 into the text box that appears.
- To connect to a remote computer, select File, and then select Connect Network Registry.
- In the Select Computer dialog box, enter the name of the remote computer, select Check Names, and then select OK.
- Open the registry and navigate to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerWinStations.
- If PortNumber has a value other than 3389, change it to 3389.
Important
You can operate Remote Desktop services using another port. However, we don't recommend you do this. This article doesn't cover how to troubleshoot that type of configuration.
- After you change the port number, restart the Remote Desktop Services service.
Check that another application isn't trying to use the same port
For this procedure, use a PowerShell instance that has administrative permissions. For a local computer, you can also use a command prompt that has administrative permissions. However, this procedure uses PowerShell because the same cmdlets work locally and remotely.
Open a PowerShell window. To connect to a remote computer, enter Enter-PSSession -ComputerName .
Enter the following command:
Look for an entry for TCP port 3389 (or the assigned RDP port) with a status of Listening.
Note
The process identifier (PID) for the process or service using that port appears under the PID column.
To determine which application is using port 3389 (or the assigned RDP port), enter the following command:
Look for an entry for the PID number that is associated with the port (from the netstat output). The services or processes that are associated with that PID appear on the right column.
If an application or service other than Remote Desktop Services (TermServ.exe) is using the port, you can resolve the conflict by using one of the following methods:
- Configure the other application or service to use a different port (recommended).
- Uninstall the other application or service.
- Configure RDP to use a different port, and then restart the Remote Desktop Services service (not recommended).
Check whether a firewall is blocking the RDP port
Use the psping tool to test whether you can reach the affected computer by using port 3389.
Go to a different computer that isn't affected and download psping from https://live.sysinternals.com/psping.exe.
Open a command prompt window as an administrator, change to the directory in which you installed psping, and then enter the following command:
Check the output of the psping command for results such as the following:
- Connecting to : The remote computer is reachable.
- (0% loss): All attempts to connect succeeded.
- The remote computer refused the network connection: The remote computer is not reachable.
- (100% loss): All attempts to connect failed.
Run psping on multiple computers to test their ability to connect to the affected computer.
Note whether the affected computer blocks connections from all other computers, some other computers, or only one other computer.
Recommended next steps:
- Engage your network administrators to verify that the network allows RDP traffic to the affected computer.
- Investigate the configurations of any firewalls between the source computers and the affected computer (including Windows Firewall on the affected computer) to determine whether a firewall is blocking the RDP port.

